Page Not Found
Page not found. Your pixels are in another canvas.
A list of all the posts and pages found on the site. For you robots out there is an XML version available for digesting as well.
Page not found. Your pixels are in another canvas.
About me
Free and Opensource Tools that can be used for Hardware Designing and Validation
Elaboration of my personal work setup
Published:
A computer needs to communicate with the external world to perform tasks. To facilitate this, we have peripheral hardware. When these peripherals need to talk to the operating system, we have interrupts. In this episode of TinyOS🐞 tutorial series, we will be looking at interrupts and how to use them.
Published:
In this episode of episode of the TinyOS🐞 tutorial series, we will be looking at how to protect critical sections in processes using spinlocks.
Published:
In the MultiTasking episode of the TinyOS🐞 tutorial series, we implemented “Cooperative Multitasking”. Next in TimerInterrupt episode, we discussed how the RISC-V time interrupt mechanism works. If you have missed them, I highly recommend going through them before proceeding.
Published:
In the previous episode MultiTasking, we implemented a operating system with cooperative multitasking. However, without the implementation of an interruption mechanism, our system cannot support preemptive multitasking.
Published:
In the previous episode ContextSwitch of TinyOS🐞, we introduced the context switching mechanism under the RISC-V architecture. In this episode we will be looking at Multitasking in our DIY operating system.
Published:
Lots of researchers have been curious about my Docker setups. Docker is actually a super handy tool for research. So, in this article, I’ll walk you through the basics of Docker for engineers/researchers.
Published:
In the previous episode HelloWorld of TinyOS🐞, we discussed how to print strings to the UART serial port for a specific processor on QEMU that utilises RISC-V architecture. This episode takes us further into the operating system territory, introducing the concept of “Context-Switching”.
Published:
Welcome to the first and simplest episode of TinyOS🐞. In this episode we will be looking at memory map settings of QEMU and writing a simple HelloWorld program. If you missed the introduction article about TinyOS🐞, you can find it here.
Published:
TinyOS🐞 is a tutorial series about minimal operating system kernel implementation based on the comprehensive tutorial series mini-risscv-os. This operating system kernel is based on RISC-V instruction set architecture. Credits goes to the original authors of mini-risscv-os. A fully built environment is available as a docker environment. This tutorial will cover several chapters related to implementing a operating system from begining.
Published:
Previously we looked at the verification of Verilog hardware implementations. In this post, we will be looking at the verification of firmware or systems code. Here the hardware implementation is abstracted with Instruction Level Abstraction (ILA). This allows us to make complex verification problems more tractable.
Published:
This simple Linux kernel tutorial is based on the book “The Linux Kernel Module Programming Guide”. We are using Ubuntu to bind the examples.
Published:
In previous post, we discussed Racket and Rosette. This is the post where we are going to verify our hardware designs using the infrastructure we have developed so far. In a nutshell, we will be looking at verifying Verilog hardware designs with Rosette.
Published:
This post is focusing on the verification with Rosette. Rosette defines extensions on Racket programming language to uplift the process of verification of implementations. We introduced Racket basics in the previous post. To make things more interesting we have used Jupyter Notebook environment. This time we will be using Rosette in the same environment, which will make verification problems much more interactive and fun.
Published:
In this post, we will be looking at basic Racket programming. At the end of the post, we will be doing some Racket programming exercises on the Jyputer environment. If you missed the previous post, where we looked at setting up the environment for the RackeTutes tutorial series, you can check it out from here.
Published:
RackeTutes is a tutorial series for Racket and Rosette solver-aided programming language to promote “Secure and validated” hardware designs.
Published:
This article is based on a talk conducted by Professor Jack Dongarra, who is a world renowned expert in numerical computing and tools for parallel computing and also the Turing Award winner in the year 2021.
Published:
So far we looked at implementing firmware for bare metal use cases. But you may have seen that in most of the hardware SDK’s, they suggest using a bootloader to load your programs.
Published:
In this episode of the firmware tutorial, let us build a firmware linker script from scratch for picoRV processor. You may remember in the previous tutorials we have used sections.lds to get the elf file. This linker file contains information about how much memory is available in our system and where and where specific hardware components use the memory so that the compiler can place different functions appropriately.
Published:
In the previous article, we looked at the different steps involved in the process of compiling firmware that is ready to run on actual hardware. For that, we have used the default firmware given in the picoRV repo. In this article, we write a very simple program from scratch to print “HELLO WORLD” to the UART output of the picoRV processor.
Published:
In this tutorial, we are going to look at writing firmware for an embedded hardware device. This tutorial is solely focused on simulations. However, it can be synthesized to work on FPGAs.
Published:
XOR neural network is one of the basic and simplest neural networks. It is trained by XOR gate input as input features and XOR gate output as the prediction. A basic XOR gate can be created using 3 layers neural network. The architecture that I have used and how I inferred it on FPGA is discussed here onwards.
Published:
This article is about two incidents that happened in the past, creating catastrophic tragedies due to mistakes in simple lines of code. Incidents like this signify the importance of verification of the systems that we build.
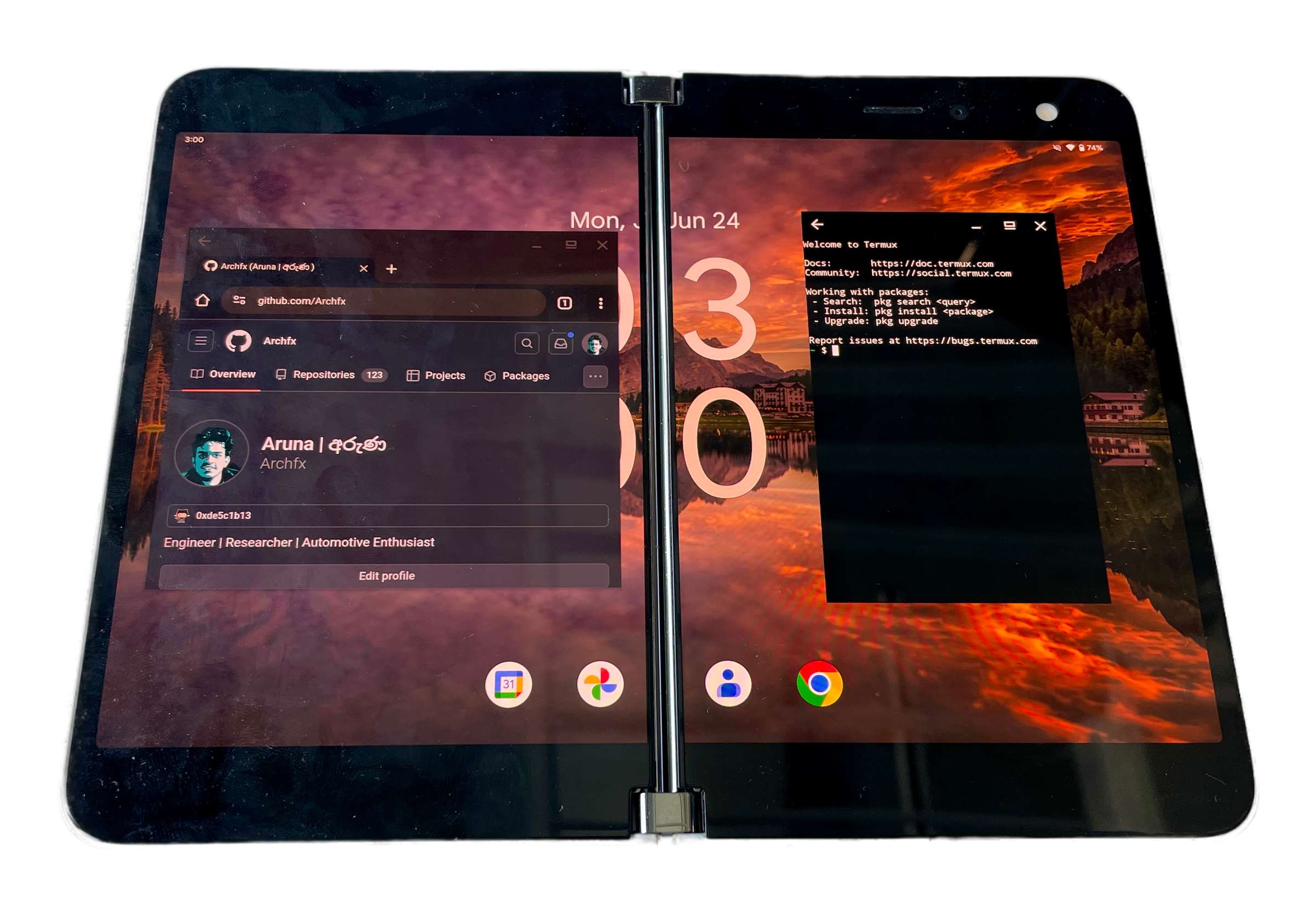
The Surface Duo, Microsoft’s dual-screen Android device, aimed to redefine mobile productivity by offering a unique form factor that combined the versatility of two screens with the familiarity of the Android operating system. Launched in September 2020, the device garnered attention for its innovative design but faced criticism for its high price, software bugs, and lack of 5G support. Despite a subsequent release of the Surface Duo 2 in October 2021, which addressed some of these issues with improved hardware and features, the devices struggled to gain significant market traction. Microsoft officially ceased updates and support for the Surface Duo line in early 2023, marking the end of its interest in the dual-screen smartphone market. However, with AOSP GSI and the help of the opensource community, we are building the Surface Duo Dual Experience (DUO-DE) custom ROM with over-the-air (OTA) update support.
 Real Time depth map generation using SSD algorithm on low end Basys 3 FPGA. Support 320x240 and 160x120 resolutions. Most of the image processing projects in academia has been done on higher-end FPGA’s with a considerable amount of resources. The main objective of this project is to implement a reliable embedded system on a lower end FPGA with limited resources. This project is based on Disparity calculation based on SAD (Sum of Absolute Difference) algorithm and creating a depth map.
Real Time depth map generation using SSD algorithm on low end Basys 3 FPGA. Support 320x240 and 160x120 resolutions. Most of the image processing projects in academia has been done on higher-end FPGA’s with a considerable amount of resources. The main objective of this project is to implement a reliable embedded system on a lower end FPGA with limited resources. This project is based on Disparity calculation based on SAD (Sum of Absolute Difference) algorithm and creating a depth map.

Test vector leakage assessment evaluates the side-channel leakage of sensitive information from the hardware implementation of a design. While TVLA for symmetric cryptography has been well studied, it is not applicable to asymmetric cryptography algorithms. Asymmetric-key algorithms involve complex computations in multiple stages that can lead to varying trace lengths depending on input parameters and associated constraints. In this article, we design an effective TVLA technique for asymmetric-key cryptosystems that can compare lengthy trace data with a good statistical resolution and generate valid input (test) patterns to satisfy specific constraints. Specifically, this article makes the following major contributions. The proposed test generation algorithm can produce valid test patterns to maximize the power signature differences. Our proposed partition-based differential power analysis can significantly improve the TVLA accuracy.

Simple Greedy algorithm AREST, which can find you the best state encoding for a given FSM that is resistant against Laser Fault Injection (LFI) attacks. Finite State Machines (FSMs) are widely used to implement complex computation sequences and communication protocols. An FSM may consist of different states with different privilege levels, such as protected and non-protected. Ideally,switching from a non-protected state to a protected state should involve an authorization transition. However, with Laser-based Fault injection (LFI), an attacker can bypass authorization by flipping bits in the FSM’s state vector. In order to mitigate LFI vulnerability, one can encode the FSM states with the objective of maintaining a large Hamming Distance (HD) between each pair of states. The existing FSM encoding algorithms are either very slow, rely on the user’s mathematical ability to manually generate certain state encodings, or lead to unacceptable area overhead.
 Design files of the simple heavy lifting drone created for Drone enduarance race Sky of Icarus. The robustness of a quadcopter frame is of paramount importance in ensuring its durability and reliable performance. A well-designed and sturdy frame is built to withstand the rigors of flight, including impacts, vibrations, and other external forces. It is typically constructed from high-quality materials such as carbon fiber or aluminum, which provide excellent strength-to-weight ratios. The frame’s design incorporates reinforcement at critical stress points, such as motor mounts and landing gear attachments, to distribute forces evenly and prevent structural failure.
Design files of the simple heavy lifting drone created for Drone enduarance race Sky of Icarus. The robustness of a quadcopter frame is of paramount importance in ensuring its durability and reliable performance. A well-designed and sturdy frame is built to withstand the rigors of flight, including impacts, vibrations, and other external forces. It is typically constructed from high-quality materials such as carbon fiber or aluminum, which provide excellent strength-to-weight ratios. The frame’s design incorporates reinforcement at critical stress points, such as motor mounts and landing gear attachments, to distribute forces evenly and prevent structural failure.
 Real-Time Kinematics (RTK) GPS is a precise positioning technology that enhances the accuracy of standard GPS systems by utilizing additional information from reference stations. Traditional GPS receivers provide location information with an accuracy ranging from a few meters to several tens of meters. However, RTK GPS offers centimeter-level accuracy by employing a base station that continuously collects data from satellites and transmits correction signals to the rover receiver in real time. These correction signals compensate for atmospheric delays and other error sources, allowing the rover to calculate its position with exceptional precision. RTK GPS finds applications in various industries, including surveying, precision agriculture, construction, and autonomous navigation. Its high accuracy and real-time capabilities enable tasks such as land surveying, machine guidance, and UAV navigation with unparalleled precision, revolutionizing industries that require precise positioning information.
Real-Time Kinematics (RTK) GPS is a precise positioning technology that enhances the accuracy of standard GPS systems by utilizing additional information from reference stations. Traditional GPS receivers provide location information with an accuracy ranging from a few meters to several tens of meters. However, RTK GPS offers centimeter-level accuracy by employing a base station that continuously collects data from satellites and transmits correction signals to the rover receiver in real time. These correction signals compensate for atmospheric delays and other error sources, allowing the rover to calculate its position with exceptional precision. RTK GPS finds applications in various industries, including surveying, precision agriculture, construction, and autonomous navigation. Its high accuracy and real-time capabilities enable tasks such as land surveying, machine guidance, and UAV navigation with unparalleled precision, revolutionizing industries that require precise positioning information.

Hardware trojan detection is a critical process that aims to identify and mitigate the presence of malicious alterations or additions in integrated circuits or electronic devices. It involves various techniques and methodologies to ensure the integrity and trustworthiness of hardware components. Hardware trojans can be inserted during the manufacturing process, and they can pose significant risks by compromising the functionality, security, and reliability of the affected systems. Detection methods range from physical inspections, such as side-channel analysis and optical inspection, to more advanced techniques like hardware fingerprinting, anomaly detection, and formal verification. By employing a combination of these approaches, hardware trojan detection plays a vital role in safeguarding critical infrastructure, preventing unauthorized access, and maintaining the trustworthiness of electronic systems. TrojanWars utilizes efficient test generation-based techniques to activate malicious implants if present in the designs.