Surface-Duo Dual Experience
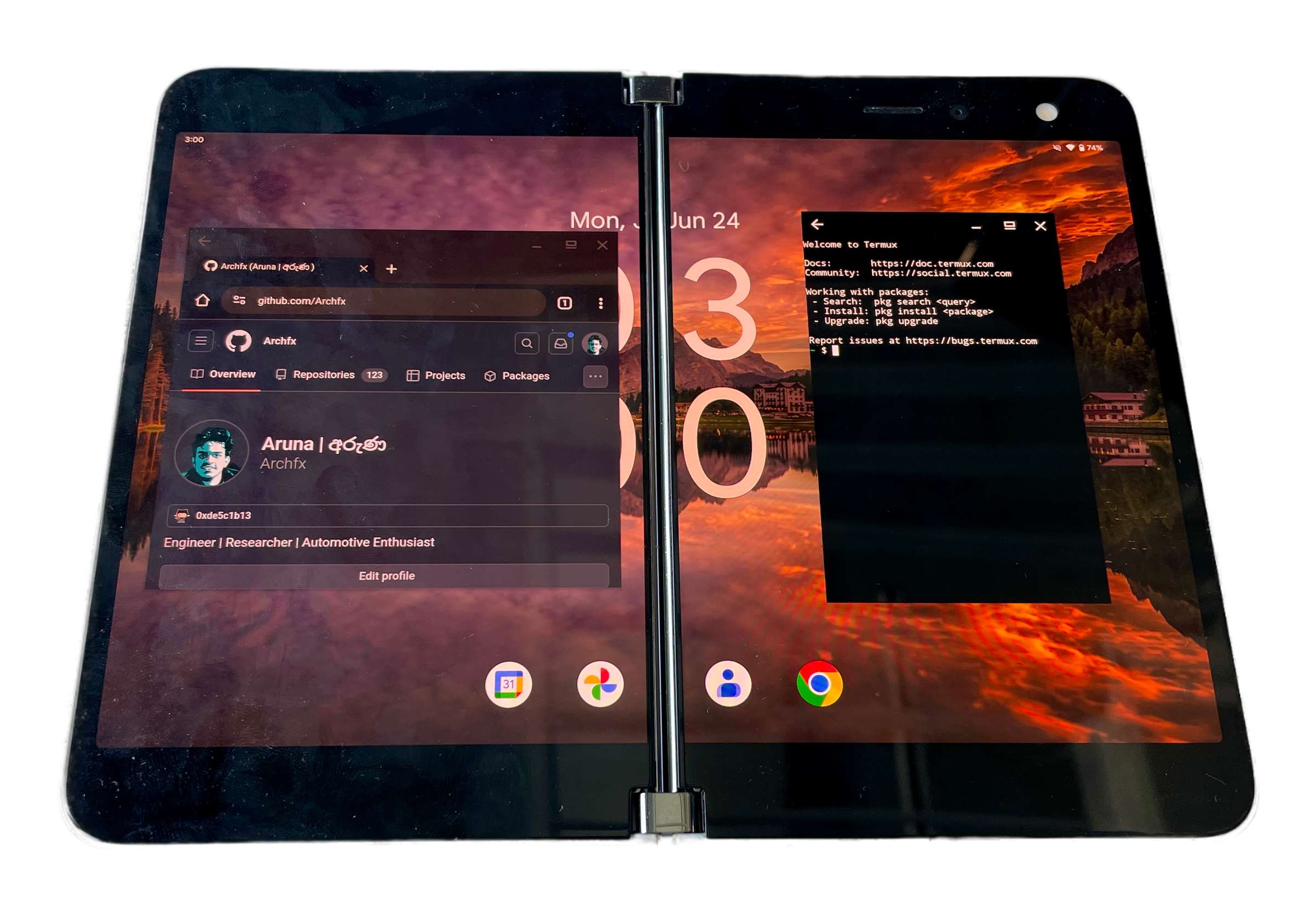
The Surface Duo, Microsoft’s dual-screen Android device, aimed to redefine mobile productivity by offering a unique form factor that combined the versatility of two screens with the familiarity of the Android operating system. Launched in September 2020, the device garnered attention for its innovative design but faced criticism for its high price, software bugs, and lack of 5G support. Despite a subsequent release of the Surface Duo 2 in October 2021, which addressed some of these issues with improved hardware and features, the devices struggled to gain significant market traction. Microsoft officially ceased updates and support for the Surface Duo line in early 2023, marking the end of its interest in the dual-screen smartphone market. However, with AOSP GSI and the help of the opensource community, we are building the Surface Duo Dual Experience (DUO-DE) custom ROM with over-the-air (OTA) update support.

 Real Time depth map generation using SSD algorithm on low end Basys 3 FPGA. Support 320x240 and 160x120 resolutions. Most of the image processing projects in academia has been done on higher-end FPGA’s with a considerable amount of resources. The main objective of this project is to implement a reliable embedded system on a lower end FPGA with limited resources. This project is based on Disparity calculation based on SAD (Sum of Absolute Difference) algorithm and creating a depth map.
Real Time depth map generation using SSD algorithm on low end Basys 3 FPGA. Support 320x240 and 160x120 resolutions. Most of the image processing projects in academia has been done on higher-end FPGA’s with a considerable amount of resources. The main objective of this project is to implement a reliable embedded system on a lower end FPGA with limited resources. This project is based on Disparity calculation based on SAD (Sum of Absolute Difference) algorithm and creating a depth map.

 Design files of the simple heavy lifting drone created for Drone enduarance race Sky of Icarus. The robustness of a quadcopter frame is of paramount importance in ensuring its durability and reliable performance. A well-designed and sturdy frame is built to withstand the rigors of flight, including impacts, vibrations, and other external forces. It is typically constructed from high-quality materials such as carbon fiber or aluminum, which provide excellent strength-to-weight ratios. The frame’s design incorporates reinforcement at critical stress points, such as motor mounts and landing gear attachments, to distribute forces evenly and prevent structural failure.
Design files of the simple heavy lifting drone created for Drone enduarance race Sky of Icarus. The robustness of a quadcopter frame is of paramount importance in ensuring its durability and reliable performance. A well-designed and sturdy frame is built to withstand the rigors of flight, including impacts, vibrations, and other external forces. It is typically constructed from high-quality materials such as carbon fiber or aluminum, which provide excellent strength-to-weight ratios. The frame’s design incorporates reinforcement at critical stress points, such as motor mounts and landing gear attachments, to distribute forces evenly and prevent structural failure. Real-Time Kinematics (RTK) GPS is a precise positioning technology that enhances the accuracy of standard GPS systems by utilizing additional information from reference stations. Traditional GPS receivers provide location information with an accuracy ranging from a few meters to several tens of meters. However, RTK GPS offers centimeter-level accuracy by employing a base station that continuously collects data from satellites and transmits correction signals to the rover receiver in real time. These correction signals compensate for atmospheric delays and other error sources, allowing the rover to calculate its position with exceptional precision. RTK GPS finds applications in various industries, including surveying, precision agriculture, construction, and autonomous navigation. Its high accuracy and real-time capabilities enable tasks such as land surveying, machine guidance, and UAV navigation with unparalleled precision, revolutionizing industries that require precise positioning information.
Real-Time Kinematics (RTK) GPS is a precise positioning technology that enhances the accuracy of standard GPS systems by utilizing additional information from reference stations. Traditional GPS receivers provide location information with an accuracy ranging from a few meters to several tens of meters. However, RTK GPS offers centimeter-level accuracy by employing a base station that continuously collects data from satellites and transmits correction signals to the rover receiver in real time. These correction signals compensate for atmospheric delays and other error sources, allowing the rover to calculate its position with exceptional precision. RTK GPS finds applications in various industries, including surveying, precision agriculture, construction, and autonomous navigation. Its high accuracy and real-time capabilities enable tasks such as land surveying, machine guidance, and UAV navigation with unparalleled precision, revolutionizing industries that require precise positioning information.